Guide to the TeRA Report
warning
Information which is deemed to be confidential and available only to current users will be marked as "See official product guide"
Receiving your TeRA report#
You will receive a link to your TeRA report via email. The email will contain a link where you can open and download the report. The email will look like this:
Click on the link (redacted in the image above) to open the report.

Structure of the report#
There are three parts to the TeRA report: Part A: Key Findings, Part B: Full Results and Appendix.
Part A: Key Findings contains an executive summary of the TeRA analysis results, key highlights for each of the threat and resilience scores, risk improvement actions and a risk action plan.
Part B: Full Results contains more comprehensive information regarding each of the risk and resilience scores, national and local historic attack details, relevant industry historic attack details, a record of all questions and answers, and risk improvement actions.
Part 4: Appendix contains additional information about the report and how to understand and interpret the results.
Part A: Key Findings#
Assessment Details#
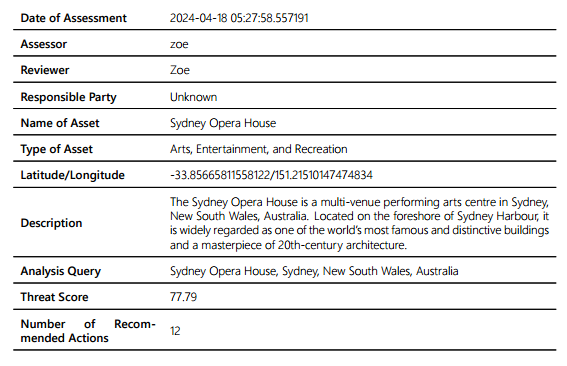
The assessment details are presented in a table which summarises all the high-level details of the assessment. This includes the date the assessment was completed, the assessor, terms used in the analysis query, and a map of the site being assessed.
Threat Score#
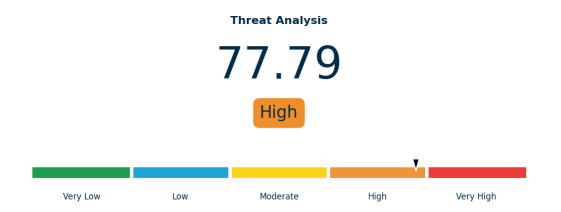
Threat is a measurement of the risk that a site will be targeted or attacked. TeRA quantifies this risk in terms of whether a site possesses features and characteristics which make it an attractive target for an attack. The threat score is determined via an algorithm which has two components: a background risk component and a site-specific risk component. These components are comprised of various features outlined in more detail below. The background risk component is determined via analysis of trends in number and type of terrorist attacks occurring globally, regionally, nationally and within the immediate vicinity of the site. The site-specific risk component is determined by gathering information on the site and analysing its online profile, its function and industry type, and the nature of where it is located.
| Criteria | Rating | Description |
|---|---|---|
| Less than 20 | Very Low | This indicates that the site possesses few or no notable features and attributes which make it an attractive target for a terrorist attack. Based on this analysis, the site falls well below the threat threshold set by TeRA through its analysis of past attacks and incidents, and the risk that the site will be targeted or attacked is rated as very low. |
| Between 20 and 40 | Low | This indicates that the site possesses some minor features and attributes which make it an attractive target for a terrorist attack. Based on this analysis, the site falls below the threat threshold set by TeRA through its analysis of past attacks and incidents, and it is unlikely to be targeted or attacked unless there is a significant change in the current threat environment or choice of targets. |
| Between 40 and 60 | Moderate | This indicates that the site possesses some features and attributes which make it an attractive target for a terrorist attack, but these features and attributes are not sufficient for the analysis to conclude that the site should be classified as high or very high risk. For this reason, the site still falls under the threat threshold set by TeRA through its analysis of past attacks and incidents. However, changes in the threat environment or choice of targets in the immediate future may increase the threat score for the site beyond the threat threshold. As such, the site should be vigilant to the threat environment and be prepared for a sudden increase in current security measures, controls and procedures. |
| Between 60 and 80 | High | This indicates that the site falls above the threat threshold set by TeRA because it possesses notable features and attributes which make it an attractive target. It is also likely that the site will remain an attractive target for terrorist groups unless there is a noticeable change in the threat environment or choice of targets in the immediate future. Due to its high threat rating, it is recommended that the asset urgently review its current security measures, controls and procedures to ensure that they are effective and up to date, as well as ensuring that any gaps and vulnerabilities are immediately addressed. |
| Greater than 80 | Very High | This indicates that the site falls well above the threat threshold set by TeRA through its analysis of past attacks and incidents. At this level, the site possesses a combination of notable features and attributes which make it a very attractive target. Due to its level of prominence, it is likely that the site will remain an attractive target into the foreseeable future. Due to its high threat rating, it is recommended that the asset urgently review its current security measures, controls and procedures to ensure that they are effective and up to date, as well as ensuring that any gaps and vulnerabilities are immediately addressed. |
Site score#
The site risk score is based on the number of online results returned for the reference name provided in the assessment. This is determined using web-scraping and search engines which provide a count of the number of references made to a site online on different websites and online sources.
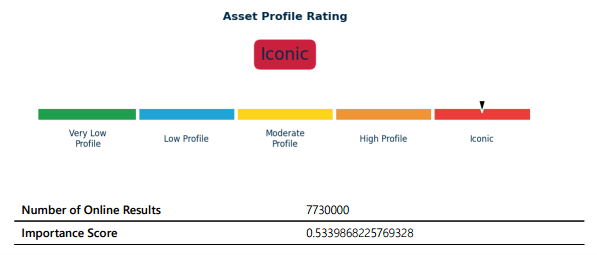
The following criteria is applied to generate a qualitative rating based on the quantitative score.
| Criteria | Rating | Description |
|---|---|---|
| See official product guide | Very Low Profile | The site has a very low profile suggesting that its location, function or connections are unknown except for those who directly interact with it or live within the immediate local area. |
| See official product guide | Low Profile | The site has a low profile suggesting that its location, function or connections are well known to those in the local area. |
| See official product guide | Medium Profile | The site has a medium profile suggesting that it would be well known at a local or state level, but it would not be well known at a national level or beyond. |
| See official product guide | High Profile | The site has a high profile suggesting that it would be very well known within the country it is located and may be recognised internationally. |
| See official product guide | Iconic | The site has a very high profile suggesting that it would be considered internationally iconic, with its location, function or connections with a particular country or group internationally recognised or known. |
High-Risk Sites in Surrounding Area#
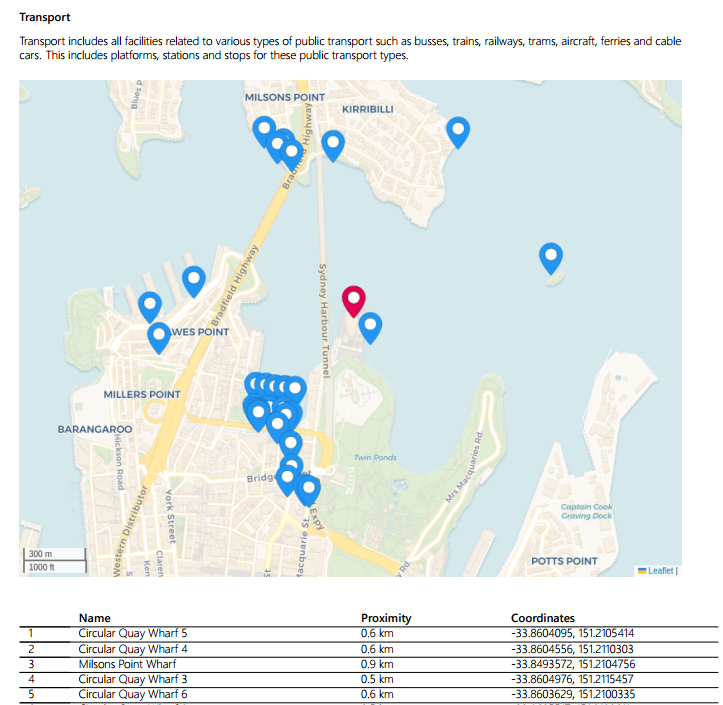
Based on the location of the site indicated during the assessment, a search of the surrounding area is performed to identify what are deemed "high-risk sites". These are sites which, based on historical data, have been frequent or popular targets of terrorist groups and include places identified as government buildings, military sites, police stations, public transport, tourist attractions, embassies, places of worship and landmarks.
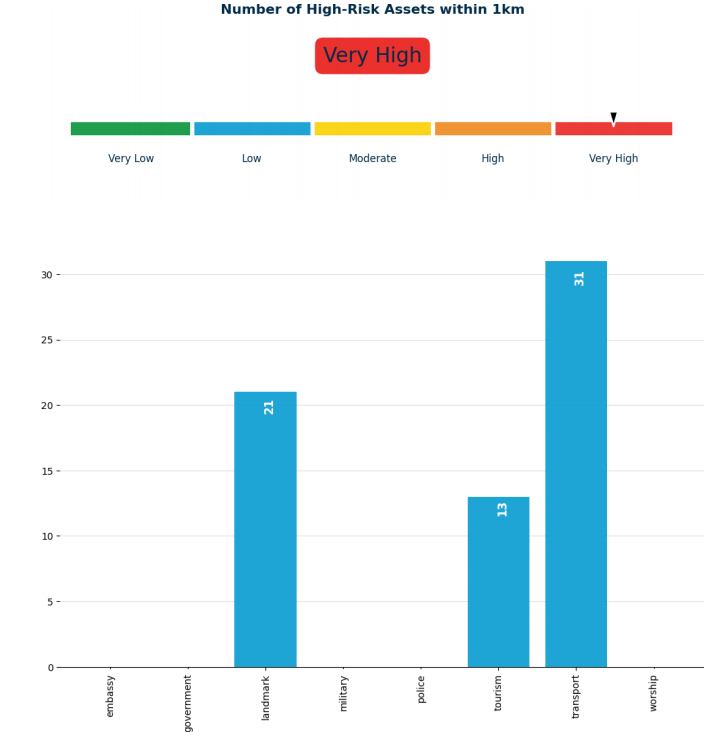
For each high-risk site type, a map is also provided with markers indicating the location of each site found.
Background Risk Score#
The background risk score is calculated using historical data of past terrorist attacks. The purpose of this score is to contextualise the risk exposure of a site based on its location and by looking at historical trends, taking into account the proportion of global terrorist attacks which have occurred within the region, the number of terrorist attacks in the region which have occurred within the country, and the number of terrorist attacks in the country which have occurred within 10km.
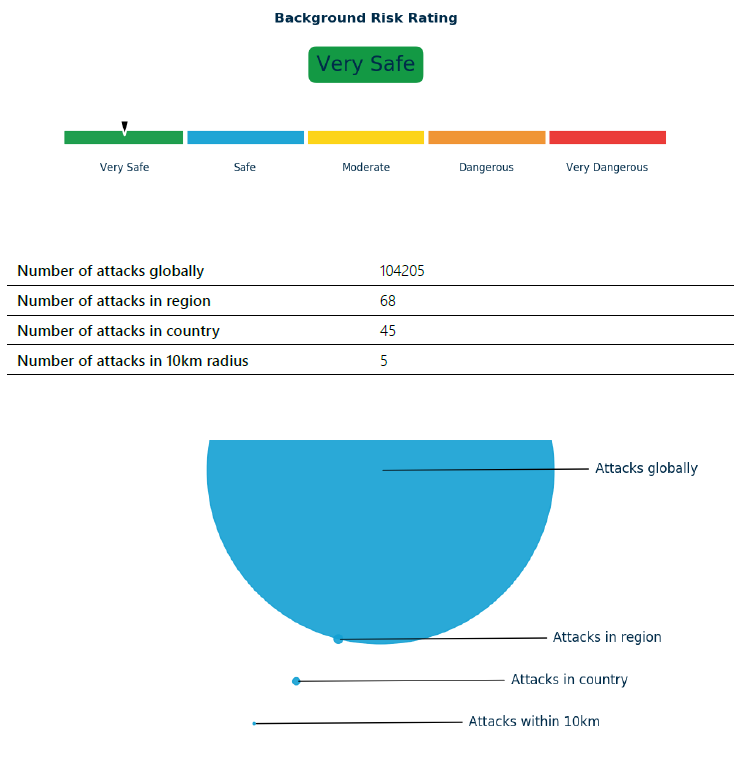
The following criteria is applied to generate a qualitative rating based on the quantitative score.
| Criteria | Rating | Description |
|---|---|---|
| See official product guide | Very Safe | The surrounding area, country and region have historically not experienced any notable levels of terrorist activity. Terrorist attacks are rare and do not happen within any regular frequency, with less than 1 attack occurring every year on average since 2001. |
| See official product guide | Safe | The surrounding area, country and region have historically not experienced any notable levels of terrorist activity. Terrorist attacks are rare but occur with some regularity with at least 1 attack occurring every year on average since 2001. |
| See official product guide | Moderate | The surrounding area, country and region have experienced high levels of terrorist activity and attacks on a regular and frequent basis |
| See official product guide | Dangerous | The surrounding area, country and region have experienced high levels of terrorist activity and attacks on a regular and frequent basis. |
| See official product guide | Very Dangerous | The surrounding area, country and region have experienced globally high levels of terrorist activity and attacks on a regular and frequent basis and at high volume. |
Resilience#
Resilience is defined as the ability for a site to recover from an incident or attack. TERA uses threat and resilience as its primary metrics for assessing terrorism risk. This differs from other methods to assess terrorism risk which typically use a combination of threat and vulnerability.
Every question related to the security measures in place are assigned to one of these seven categories. A user’s answer to a question is converted into one of two response types: a positive or a negative response. A positive answer means that the answer reflects a positive impact on the risk of the site, that is, it decreases its vulnerability or risk exposure. A negative answer means that an answer reflects a negative impact on the risk of the site, that is, it increases its vulnerability or risk exposure. This conversion is necessary as there are instances where an answer to a question, such as “yes”, will be considered positive (e.g. “Do you have CCTV cameras in place”) and other instances where it will be considered negative (e.g. “Is the site exposed to vehicle traffic”).
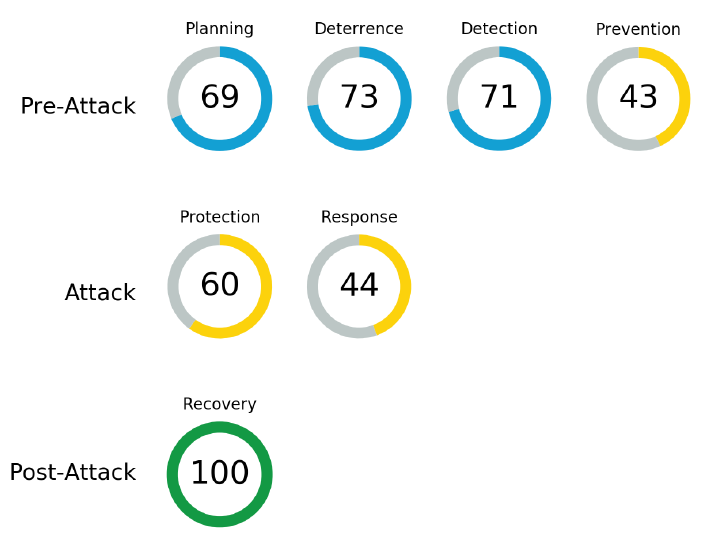
The resilience scoring comprises of seven categories: planning, deterrence, detection, prevention, protection, response, and recovery.
Resilience Scoring#
The report will provide a score for each of the seven resilience categories. The categories themselves are grouped together into Pre-Attack, Attack, and Post-Attack to match the phases of an attack where that resilience category would be most relevant.
The resilience score for a given category is determined according to the following formula:
Where P is the total number of questions in a category with a positive response, T is to the total number of questions grouped in a category, and NA is the total number of questions in a category with a “Not Applicable” response, and c is one of the seven categories.
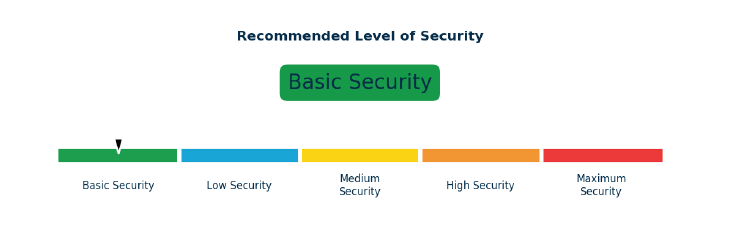
Recommended Level of Security#
The recommended level of security is generated based on a site’s threat and vulnerability ratings and correlates with the risk improvement actions provided. The score determines the level of security mitigation measures a site ought to adopt in its protection from a terrorist threat.
Risk Improvement Actions#
Each question has a corresponding recommended action (also referred to as a “risk improvement action”), which is inserted if the question is answered in the negative. If a question is answered in the positive, the corresponding recommended action is not included.
warning
The recommended actions used in the standard version of TeRA have been taken from the security controls and measures outlined in ‘FEMA 452’ (2017) from the US Department of Homeland Security, the ‘Crowded Places Security Audit’ (2017) from the Australia New Zealand Counter Terrorism Committee, and the ‘Publicly accessible locations guidance’ (2022) from ProtectUK.
The actions themselves, as well as the method for selecting and grouping these actions may be further customised by the user to meet their specific requirements.
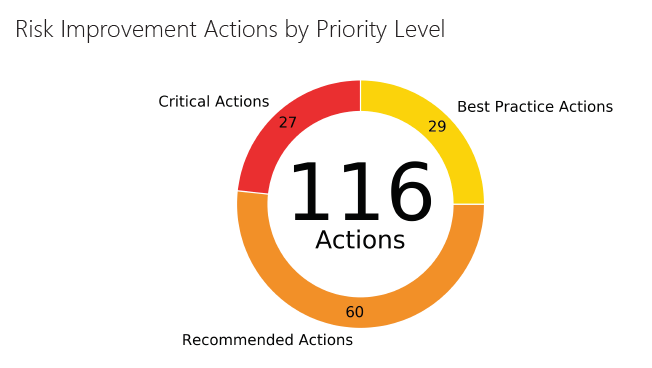
Each recommended action is assigned one of three priority levels: critical, recommended and best practice.
| Priority | Description |
|---|---|
| Critical | A critical action encompasses fundamental or essential measures and controls that are critical to the effective management of security risks and threats. These critical actions should be prioritised for immediate implementation as without them the defensive capability of a site is severely compromised. Critical measures and controls can be considered the minimum standard for effective management of security risks and threats and are therefore relevant for all sites regardless of threat rating. |
| Recommended | Recommended actions improve defensive capability and effectiveness against security risks and threats beyond a basic or essential level. A site will typically implement a selection of these recommended actions to enhance its defensive capability based on specific security requirements and threat ratings. The number of recommended actions that should be in place increases as the threat level increases. |
| Best Practice | Best practice actions provide specialised capability or improvements to security in particular scenarios and sites. These measures and controls are highly specialised and address specific threats and risks that may not be relevant for all sites or scenarios. Best practice measures and controls are most relevant for sites where the threat rating is high or very high. The higher risk level justifies the deployment of more specialised measures and controls to provide additional defensive capability. |
This designation varies depending on the threat score. For example, an action “Install CCTV cameras at all entrances and exits” may be designated as critical if the threat score is Very High, High, recommended if it is Moderate and best practice if it is Low or Very Low. An example is demonstrated below:
| Action | Very Low | Low | Moderate | High | Very High |
|---|---|---|---|---|---|
| A1 Plans are to be extended to cover the entire route. In particular, the plan must identify all potential risks across the entirety of the route and determine possible controls that could be implemented. | Best practice | Best practice | Best practice | Recommended | Recommended |
The complete mapping of recommended actions to priority level based on threat rating can be provided for users upon request.
The report generates a chart which provides the number of risk improvement actions in each priority:
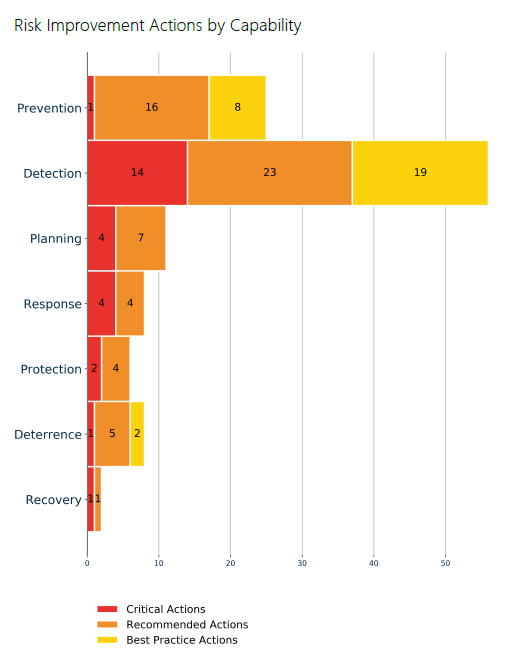
And an additional chart showing the number of actions per priority and per resilience category:
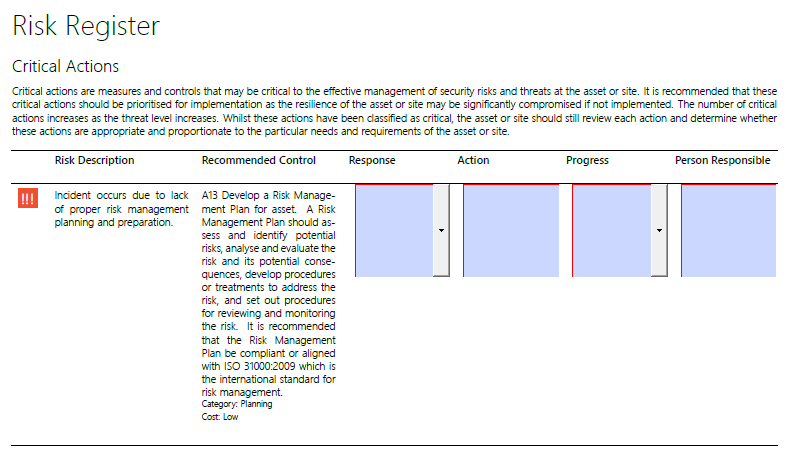
Risk Register#
The report also contains an auto-generated risk-register. This risk register provides a risk description, corresponding recommended control/action, and interactive fields for tracking response, action, progress and person responsible.
Part B: Full Results#
In Part B of the report, each risk and resilience score is explained, clarifying the qualitative and quantitative meaning of each result.
Additionally, Part B: Full Results includes a full record of the questions and answers from the assessment, along with further details for each question. The additional details provide recommended security policies and procedures and provide a reference to the relevant standard or guidance from which the question was sourced.
